Spam filtering software based on keywords, etc. is only one brick in the wall guarding against Spam; another one is to implement black- or block-list support within your messaging and collaboration environment. With the new release of Exchange, Microsoft implemented the functionality to filter every incoming email whether the sender is on a blacklist or not. Within this article you will learn how blacklists work and how you can configure support with
Exchange Server 2003.
But Spam filtering software based on keywords, etc. is only one brick in the wall guarding against Spam; another one is to implement black- or block-list support within your messaging and collaboration environment. With the new release of Exchange, Microsoft implemented the functionality to filter every incoming email whether the sender is on a blacklist or not.
Learn how blacklists work and how you can
configure Exchange Server 2003.
What are blacklists and how do they work?f you perform a search with an internet search engine you will find lots of blacklist providers throughout the world. This means, the first thing you have to do is consider what blacklist provider you want to use. Nobody can say this or that blacklist provider is the best, you should make your own experiences but if you have a look at the recommendations of the IT press and testing results published in these magazines one of the following blacklist providers may be a good choice.
* relays.ordb.org
* relays.visi.com
* bl.spamcop.net
* blackholes.wirehub.net
* list.dsbl.org
If you have a look at one of these blacklist provider’s websites you will find an explanation on how blacklists work.
Each blacklist server is a special kind of service that can be compared with DNS services. If the SMTP-domain is on the blacklist it reports return status codes back to the checking messaging system providing special IP addresses.
Here is a list of the codes and what they mean:
127.0.0.2 è Open relay
127.0.0.3 è Dialup spam source
127.0.0.4 è Confirmed spam source
127.0.0.5 è Smarthosts
127.0.0.6 è Spamware software developer or spamvertized site (spamsites.org)
127.0.0.7 è Listserver that automates opts users in without confirmation
127.0.0.8 è Insecure formail.cgi script
127.0.0.9 è Open proxy server
By default, Exchange Server 2003 blocks all mails with one of these codes, but you can also configure the behavior as you want.
Configuring blacklist support with Exchange 2003
In Exchange Server 2003 you can find the feature for blacklist support within the global settings of your organization.
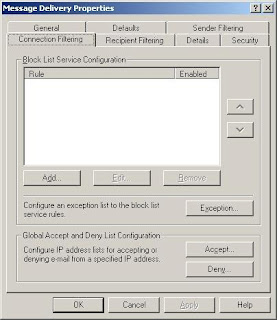
As seen above, you can implement multi-blacklist provider rules and put them in your own sequence. Exchange Server 2003 then checks every configured blacklist before it reroutes the email.
If you choose the button “Add” the following window opens:
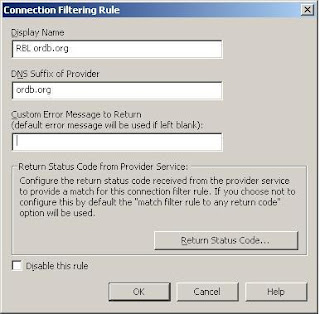
In the field “Display Name” you should put in a brief description of the rule, in the second field you have to put in the DNS suffix of the blacklist provider itself. And by default, every return status code means a blocking of that email. If you are having trouble with your blacklist provider, just disable the rule by choosing the appropriate button.
If you want to configure a customized return status code behavior, make your choice and the following window will open and will provide your customized configuration.
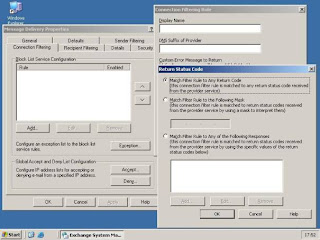
“Match Filter Rule to any return code” is the default setting and provides a blocking of every email that has a return status code. If you choose “Match Filter Rule to the Following Mask”, you can implement your own status code mask, provided by the blacklist company. If you need to implement customized return status codes, you have to choose the third radio button and then add your codes as shown below:
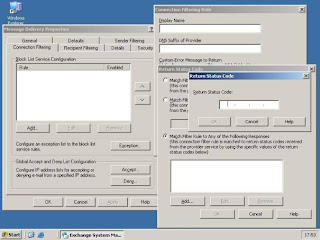
No rule without exceptions … Therefore you have a way to put in your exceptions by choosing the appropriate button. If you want to configure global IP accept and/or deny lists, this is possible, too. Just choose the “Accept” or “Deny” button.
The next step is now to check if everything runs. If it does not, in general the reason is not your
Exchange Server 2003; check your DNS- and firewall settings. The Event log may be your friend, too.
But which servers in your messaging environment should have blacklist blocking enabled? Well, that is quite easy to say: that ones that receive email directly from the internet or via a smart- or relay host within your DMZ. It should be a server that reroutes every incoming email in your organization, and if there is more than one “front-end” server in your environment, you should configure all of them. In addition, don’t forget to check the filtering directory, if there are mails from companies that are on blacklists by accident. In general their entries will be deleted within 24 hours, but within that time window your users do not receive any email from that company.
Source:http://www.msexchange.org/tutorials/Blacklist_Support_Exchange_2003.html












